November 19th, 2025 by admin
Leading MTSP Protects IT and Voice
Networks to Ensure Organizations
Are Properly Connected with
Customers
CONCORD, CA - ATS , a leading managed
technology services provider
(MTSP), announced today that it has
launched a new layer of
cybersecurity designed...
Read Full Story »
Tags: security, voice, VoIP
Posted in: Press Releases
October 1st, 2024 by admin
In our hyper-connected digital era, usernames and passwords serve as virtual keys, granting access to a company's most critical applications, online services, and sensitive data. However, these digital credentials are incredibly valuable commodities...
Read Full Story »
Tags: dark web protection, network, security threats, security
Posted in: Security, Cyber Security
May 20th, 2024 by admin
In the digital era, cybersecurity has become a paramount concern for businesses of all sizes. As companies increasingly rely on technology and online systems, the risks posed by malware and phishing attacks have escalated. These cyber threats can...
Read Full Story »
Tags: anti-virus, business, email filtering, security
Posted in: Security, Cyber Security
December 1st, 2023 by admin
Security systems have come a long way from the good old alarms that would ring a bell when someone entered your premises in the dead of the night without an invite.
Cloud video surveillance involves the use of cameras that capture video footage...
Read Full Story »
Tags: cloud, security, Video Surveillance
Posted in: Cloud Solutions, Infrastructure and Cabling
November 16th, 2023 by admin
In the digital age, email has become the lifeblood of business communication. The channel helps build relationships with clients and make final decisions, and vital information flows through it.
However, this essential tool is also a prime...
Read Full Story »
Tags: business, email filtering, security threats, security
Posted in: Cyber Security
May 19th, 2023 by admin
Technology Assurance Group Recognizes ATS Communications as the Elite Provider at their 22nd Annual Convention
CONCORD, CA – ATS, a leading managed security and IT services provider, announced today that the company received Technology Assurance...
Read Full Story »
Tags: Award, security, Solutions, TAG, technology
Posted in: Press Releases
April 25th, 2023 by admin
Video surveillance solutions for businesses are used to monitor and protect facilities, employees, inventory, the
public, and much more. These systems provide a variety of features, such as motion detection, facial
recognition,...
Read Full Story »
Tags: infrastructure, security, Solutions, Video Surveillance
Posted in: Security
April 4th, 2023 by admin
Unified Communications as a Service (UCaaS) is an all-in-one communications solution that combines voice, video, messaging, and collaboration functions into a single platform. UCaaS enables users to communicate using any device or application from...
Read Full Story »
Tags: Cloud-Based Technologies, collaboration, managed services, mobility, productivity, security, UCaaS, unified communications
Posted in: Solutions
February 22nd, 2023 by admin
Multi-factor authentication (MFA) is an extra layer of security used to ensure that only authorized individuals can
access a system or application. This type of security requires users to provide more than one form of
authentication,...
Read Full Story »
Tags: data protection, data recovery, data security, managed IT services, password, security
Posted in: Managed IT Services
February 10th, 2023 by admin
Cyber security awareness training is a program designed to educate employees about the risks of cyber-attacks and other digital threats, the importance of establishing secure online practices, and how to respond if they become victims of an attack....
Read Full Story »
Tags: cyber security, data protection, data security, IT Consulting, IT Support , managed IT services, security, services, Solutions
Posted in: Services
January 24th, 2023 by admin
Leading MTSP Shares Why Email Is an Easy Way to Destroy A Company's Network
CONCORD, CA - ATS Communications, a leading managed technology services provider (MTSP), recently announced that they are protecting small to mid-sized businesses (SMBs) with...
Read Full Story »
Tags: anti-virus, cyber security, data protection, data security, password, security
Posted in: Press Releases
January 24th, 2023 by admin
Dark web scanning is the process of actively seeking out publicly available data related to an organization, its employees, customers, vendors, or partners on the dark web. This process looks for indicators that could be used by malicious actors to...
Read Full Story »
Tags: cyber security, data protection, data security, security, services
Posted in: Managed IT Services
December 16th, 2022 by admin
Antivirus and email filtering are important tools in keeping your computer safe from malicious activity. By regularly performing security scans and monitoring incoming emails, these programs can help protect you from online threats such as viruses,...
Read Full Story »
Tags: cyber security, data protection, data security, email, hacking, malware, security, Solutions
Posted in: Security
September 21st, 2022 by admin
Leading MTSP Shares How to Protect Businesses from Cybercrime
CONCORD, CA - ATS Communications, a leading managed technology services provider (MTSP), is educating small to mid-sized business (SMB) owners on how they can protect their organizations...
Read Full Story »
Tags: cyber security, data protection, hacking, Press Release, ransomware, security, service, Solutions
Posted in: Press Releases
March 31st, 2022 by admin
Businesses across industries invest a lot of time and put in hard work to ensure their network's health and performance. After all, if something goes wrong with the system, the productivity of your business is likely to suffer. But with...
Read Full Story »
Tags: business, collaboration, managed services, security, Solutions
Posted in: Services
April 1st, 2021 by admin
For more than 40 years, ATS has provided innovative technology to California businesses. We pride ourselves on our reputation of designing, implementing, and proactively supporting solutions for clients. Our technology solutions provide companies...
Read Full Story »
Tags: cloud, cloud communications, Cloud Services, Cloud Solutions, Cloud Voice, collaboration, Communication, cyber security, data protection, Mobile Workforce, ransomware, remote office, security, services, Solutions, unified communications
Posted in: Cloud Solutions, Services, Solutions
February 23rd, 2021 by admin
Leading Managed Technology Services Provider Educates Businesses on Dramatic Increase in Cybercrime Directed at Small-Business Owners and How to Prevent It
CONCORD, CA - ATS Communications, a leading managed technology services provider (MTSP),...
Read Full Story »
Tags: ATS, business, collaboration, Communication, COVID-19, IT, Microsoft Teams, remote office, security, technology
Posted in: Managed IT Services, Press Releases, Consultation
January 20th, 2021 by admin
Many businesses have found themselves making the switch to the cloud, and when you look at everything it offers it's
not hard to see why. They give a wealth of benefits that most would be hard-pressed to ignore, such as improved
security...
Read Full Story »
Tags: disaster recovery, network security, network, security, wireless infrastructure
Posted in: Cloud Solutions, Managed IT Services, Cyber Security
January 13th, 2021 by admin
Leading Managed Technology Services Provider Educates Businesses on Dramatic Increase in Cybercrime Directed at Small-Business Owners and How to Prevent It
CONCORD, CA - ATS Communications, a leading managed technology services provider (MTSP),...
Read Full Story »
Tags: business continuity, cloud, cyber security, data protection, network security, Press Release, ransomware, security, Solutions
Posted in: Press Releases, Solutions
December 31st, 2020 by admin
Many companies have made the switch to remote working this year due to the pandemic, doing their best to adapt to changing work culture. However, the struggle doesn't end with just establishing your remote operations. Now that you've reacted, it's...
Read Full Story »
Tags: business continuity, cloud, cloud communications, Cloud Services, Cloud Solutions, collaboration, Communication, COVID-19, cyber security, data protection, Mobile Workforce, mobility, network security, productivity, remote office, security, services, Solutions, technology, unified communications, video conferencing
Posted in: Cloud Solutions, Services, Security, Solutions
July 23rd, 2020 by admin
Companies made the switch to remote work to keep employees safe from COVID-19, and with the pandemic still affecting businesses, long-term remote work appears to be the solution. Ensuring your employees have the tools and infrastructure to be successful...
Read Full Story »
Tags: collaboration, infrastructure, productivity, remote office, security
Posted in: Services, Solutions
June 9th, 2020 by admin
With businesses moving to a remote workforce, they face different challenges that they didn't deal with before. One of those challenges is how to keep your network secure while operating under a remote model. Here are some recommendations to ensure...
Read Full Story »
Tags: anti-virus, business, cyber security, data protection, email, password, security threats, security, Solutions, technology
Posted in: Services, Security, Solutions
February 27th, 2020 by admin
With each passing year progressively, more businesses are switching over to the Cloud. Yet there are still companies that haven't made the leap or taken advantage of this innovative technology. Many business owners are still hesitant to shift...
Read Full Story »
Tags: cloud, Cloud Solutions, disaster recovery, security
Posted in: Cloud Solutions, Solutions
January 16th, 2020 by admin
Protecting your data networks is one of the most important things your company can do. At ATS, our
experience and expertise enable us to bring the most innovative cybersecurity solutions to the table.
There are numerous types of cyberattacks,...
Read Full Story »
Tags: data protection, security threats, security
Posted in: Services, Security
January 9th, 2020 by admin
Network security is a hot topic nowadays, and rightfully so. Protecting your data networks from hackers is one of the most important things your business needs to do. But, has your company taken the necessary steps to protect its physical location,...
Read Full Story »
Tags: security threats, security, Video Surveillance
Posted in: Security, Solutions
November 21st, 2019 by admin
As cyber-attacks continue to intensify, businesses are having a hard time finding skilled cybersecurity workers to protect their operations. The cybersecurity industry has taken a significant hit with the labor shortage causing many companies to fall...
Read Full Story »
Tags: anti-virus, cyber security, data protection, firewall, investment, IT Support , IT, malware, managed IT services, managed services, News, security threats, security, Solutions
Posted in: Managed IT Services, Support, Services, Security, Solutions
October 2nd, 2019 by admin
Concord, CA – Announcing the launch of a Secure WiFi-as-a-Service program to protect our customers from cyber attacks through wireless access points. Over the past few years, the prevalence of cyber attacks has continued to grow, expanding...
Read Full Story »
Tags: cyber security, IT, security, technology, Wi-Fi, wireless infrastructure, wireless internet
Posted in: Press Releases, Cyber Security
August 3rd, 2019 by admin
CONCORD, CA –
We are proud to announce that we are alerting small to midsized businesses (SMBs) about the prevalence of robocall scams and how any organization can best handle these calls to ensure that all sensitive company information...
Read Full Story »
Tags: business, Communication, security, technology
Posted in: Press Releases
July 14th, 2019 by admin
It is common for companies to underestimate their security risks and think that specific attacks could never happen to their business until it happens. While it is always essential to stay prepared no matter the likelihood of an attack,...
Read Full Story »
Tags: cyber security, IT, security
Posted in: Security, Solutions
May 25th, 2019 by admin
Phishing attacks occur when communication that appears to be reputable is fraudulent. These sorts of scams are made to extract personal and sensitive information from victims such as social security numbers, addresses, bank information, and more. People...
Read Full Story »
Tags: cyber security, email, ransomware, security threats, security
Posted in: Security
May 9th, 2019 by admin
Throughout 2018 data breaches were a typical story from corporations of every size. The stories either tell of a breach that happened during the year or they're about ones that occurred years ago. Those common press releases about how their client's...
Read Full Story »
Tags: cyber security, data protection, security threats, security
Posted in: Services, Security
April 15th, 2019 by admin
CONCORD, CA – We are helping small to mid-sized businesses (SMBs) to take advantage of dramatically increased capabilities in surveillance cameras. As security, both online and offline, has become a growing concern for many small business owners,...
Read Full Story »
Tags: ATS Communications, security, technology, Video Surveillance
Posted in: Press Releases
February 5th, 2019 by admin
CONCORD, CA –
We are proud to announce a new solution to help small to midsized businesses (SMBs) equip themselves with the necessary cybersecurity protections that every modern company needs to survive. In the past, large organizations...
Read Full Story »
Tags: cyber security, IT, security, Solutions
Posted in: Press Releases
January 29th, 2019 by admin
Your business needs a dependable and robust cybersecurity solution, plain and simple. As technology continues to advance and new threats are coming to the forefront, it is essential to have the proper security and management behind you to ensure...
Read Full Story »
Tags: cyber security, safety, security reporting, security threats, security
Posted in: Security
November 15th, 2018 by admin
Security for your business is crucial. Everyone knows that, but settling for any old security system won't give you the protection you need against modern-day cybercriminals stealing sensitive data and monitoring operations. ATS offers great network...
Read Full Story »
Tags: network security, ransomware, security threats, security
Posted in: Security
July 5th, 2018 by admin
Did you know email can be a huge security risk for your businesses? Careless or unaware employees can click on malicious emails, opening up your network to security issues and downtime while it is being repaired.
ATS offers easy and affordable anti-virus...
Read Full Story »
Tags: cyber security, email, security
Posted in: Services
July 3rd, 2018 by admin
If your business is considering a Bring Your Own Device environment, there's a great deal of security preparation work to do beforehand. A successful BYOD strategy and BYOD policy is all about finding the sweet spot of control, where your business is...
Read Full Story »
Tags: cloud, Cloud-Based Technologies, Cloud Services, proactive maintenance, security
Posted in: Solutions
June 26th, 2018 by admin
Making the switch to a Bring Your Own Device (BYOD) business environment extends well beyond the decision to let employees choose their devices. Your business should look at the pros and cons of the concept before deciding how to approach it and to what...
Read Full Story »
Tags: IT Support , IT, security threats, security
Posted in: Support
June 20th, 2018 by admin
Businesses have more to worry about than ever when it comes to dealing with new forms of cyber-attacks. The shift to a BYOD workplace adds even more challenges to protecting your digital assets. While hardware and software solutions continue to improve...
Read Full Story »
Tags: IT Support , IT, security threats, security
Posted in: Support, Security
June 10th, 2018 by admin
As a business with a highly mobile workforce, you need File Sync and Share (FSS) solutions that are not going to leave your important business data exposed. With people being more and more on the move and often switching between devices, from desktop...
Read Full Story »
Tags: Cloud Solutions, control, datto drive, file sync and share, FSS, mobile, security
Posted in: Solutions
May 14th, 2018 by admin
Technology improvements have made it easy for employees to get work done on their personal devices from anywhere. However, that freedom comes with additional security risks and requires extra diligence to keep data secure. Safeguarding information is...
Read Full Story »
Tags: cyber security, security threats, security
Posted in: Security
May 3rd, 2018 by admin
Often, businesses don't prepare for email disasters until after one has hit. But while email may comprise just a small part of a company's day-to-day operation, an email disaster can have a staggering impact on your business. The 2016 Democratic National...
Read Full Story »
Tags: data protection, data recovery, data security, email, security threats, security, services
Posted in: Security, Solutions
March 26th, 2018 by admin
While all employees need to be mindful of security, the nature of C-level executives makes them more attractive targets for hackers. That means it's necessary for them to take greater precautions.
According to TechRepublic, C-level executives are more...
Read Full Story »
Tags: business, cyber security, data protection, data security, security threats, security, Solutions
Posted in: Security
March 19th, 2018 by admin
As a business owner, ATS knows that your number one priority is the safety and security of your employees and assets. Whether you want to ensure that you’re covered in case of theft, vandalism or other crime or you just want the freedom to check...
Read Full Story »
Tags: ACC, Avigilon, security, surveillance
Posted in: Solutions
March 13th, 2018 by admin
The Mirai botnet refers to a massive-scale network of Linux-running Internet of Things devices turned into remote-controlled bots through a malware infection. Hackers can use the network to run a distributed denial of service, or DDoS, by having the infected...
Read Full Story »
Tags: cyber security, hacking, malware, security threats, security
Posted in: Security
February 12th, 2018 by admin
At the end of 2017, the world learned about Spectre and Meltdown: two far-reaching security threats that exploit how CPUs work to expose protected information on nearly every recent PC, server and smartphone. Hackers can use these exploits to do things...
Read Full Story »
Tags: data protection, data security, hacking, IT Support , IT, security threats, security
Posted in: Security
February 5th, 2018 by admin
Businesses have a lot to gain by hiring remote employees, including the ability to recruit from a larger talent pool and the potential for less expensive workplace accommodations. However, remote employees introduce new challenges in IT security because...
Read Full Story »
Tags: IT Support , IT, network security, remote office, remote workers, security
Posted in: Solutions
January 29th, 2018 by admin
Financial services companies should embrace a healthy dose of caution when implementing new fintech in their business. Fintech, or any technological innovation in the financial sector, is not inherently more or less secure than any other new technology,...
Read Full Story »
Tags: cyber security, hacking, IT Support , IT, security threats, security
Posted in: Security
January 16th, 2018 by admin
Hot off the tail of the massive 2017 Equifax breach that exposed personal information of 143 million customers, businesses are on high alert concerning IT security in 2018. While the IT security industry has been successful in mitigating and cracking...
Read Full Story »
Tags: anti-virus, hacking, IT Consulting, IT Security, IT Support , IT, security threats, security
Posted in: Security
December 28th, 2017 by admin
Avoid costly data security breaches by training your staff to check for secure connections when handling private information on the Internet. Secure Hyper Text Transfer Protocol, or HTTPS, is a technology legal, healthcare, and financial businesses use...
Read Full Story »
Tags: data protection, data security, security, Solutions
Posted in: Security, Solutions
October 24th, 2017 by admin
A new spear phishing technique, being used in a hacking campaign called FreeMilk, takes advantage of a Microsoft Office vulnerability in order to hijack existing email conversations to spread malware to high-profile targets. This new technique phishing...
Read Full Story »
Tags: desktop management, hacking, security threats, security
Posted in: Security
October 3rd, 2017 by admin
The 2017 Equifax hack is teaching a painful lesson about the necessity of businesses keeping up with software patches for IT security and to avoid catastrophic damage. The hack, which resulted in potentially exposing the financial information necessary...
Read Full Story »
Tags: IT Consulting, IT Security, IT Support , IT, security threats, security
Posted in: Security
July 25th, 2017 by admin
In June 2017, WikiLeaks released secret documents that exposed the tools the CIA uses to infiltrate public and private networks through routers. These documents have shined a light on how easy it is for someone to hack a router.
This begs the question,...
Read Full Story »
Tags: network security, network, security threats, security
Posted in: Managed IT Services, Security
July 11th, 2017 by admin
If your business is using 2-factor authentication or 2FA, methods to secure your important accounts, you may need to investigate better ways to implement the practice. Security experts widely recommend using 2FA, a system which utilizes a second security...
Read Full Story »
Tags: hacking, IT Consulting, IT Security, IT Support , IT, security threats, security
Posted in: Security, Knowledge
June 27th, 2017 by admin
Getting caught off-guard in a cyber security attack is a disaster for any business, large or small—and the frequency of attacks is only getting worse.
According to the CyberEdge 2017 Cyberthreat Defense Report, hackers successfully compromised...
Read Full Story »
Tags: cyber security, data protection, data security, security threats, security
Posted in: Support, Security
June 13th, 2017 by admin
Many small-to-medium businesses (SMBs) have taken to hosting their own intranet to increase productivity in the workplace. For those unfamiliar with the term, "intranet" is not a typo, but rather an internal network that behaves like a private Internet....
Read Full Story »
Tags: collaboration, intranet, IT Consulting, productivity, security, services
Posted in: Solutions
May 23rd, 2017 by admin
When trying to determine if a piece of technology is simply old or completely obsolete, keep in mind that there are different criteria for Android and iOS devices than for desktop and laptop computers. An employee stuck using an obsolete device is likely,...
Read Full Story »
Tags: IT Assessment, IT Consulting, IT Support , IT, security
Posted in: Support, Solutions
May 10th, 2017 by admin
It happens to everyone: You turn your computer back on after you intended to leave the office, or come in early to get a head start on a new project, only to be greeted by a 20-minute operating system (OS) update session. This common workplace frustration...
Read Full Story »
Tags: advice, security
Posted in: Solutions
April 26th, 2017 by admin
Email and social media accounts provide a wealth of cyber security challenges for businesses. Hackers often look for exploits in account operations to steal information and seize control—both of which can be extremely damaging and difficult to combat....
Read Full Story »
Tags: cyber security, security
Posted in: Security
March 27th, 2017 by admin
We’ve been noticing an alarming trend regarding cyber security. Actually, more so a lack of security. One of the best practices on the frontline of security is your password. Unfortunately, this is an area that a lot of people will gloss over, often relying...
Read Full Story »
Tags: cyber security, password, security threats, security
Posted in: Services, Security
March 9th, 2017 by admin
Network-Attached Storage (NAS) servers are a great asset for small businesses managing data. For the uninitiated, NAS is essentially a streamlined server designed specifically for sharing files between devices.
Because of their simplified...
Read Full Story »
Tags: backup, Backup Solutions, data protection, data recovery, data security, IT Consulting, IT Security, IT Support , IT, security
Posted in: Managed IT Services, Knowledge
February 15th, 2017 by admin
It's a familiar sighting in the workplace: the employee with half a dozen sticky notes attached to their computer monitor. While not the most confidential or elegant solution, these employees are on to something.
Fortunately, technology has stepped in...
Read Full Story »
Tags: advice, consulting, productivity, security
Posted in: Solutions, Knowledge
January 24th, 2017 by admin
Unlike most IT security threats, phishing scams attack the human element instead of the machine element. Phishing scams try to bait a person into exposing confidential information by posing as a legitimate, reputable source, typically by email or phone....
Read Full Story »
Tags: cyber security, IT Security, security threats, security
Posted in: Security, Solutions
January 11th, 2017 by admin
For anyone unfamiliar with the Google Applications platform, Google Docs et al. are a Cloud-based spin on mainstay office suite programs that can help your staff work better together.
With a zero-dollar price tag (compared with Microsoft Office's...
Read Full Story »
Tags: cloud, Cloud-Based Technologies, Cloud Services, Cloud Solutions, IT Security, IT, productivity, security
Posted in: Cloud Solutions, Support
December 21st, 2016 by admin
Phishing attacks are a dangerous and devastating method hackers use to steal personal information and accounts—primarily by striking the user instead of the machine. According to the APWG Phishing Activity Trends Report, the first quarter of 2016 saw...
Read Full Story »
Tags: cyber security, IT Consulting, IT Security, IT Support , IT, managed IT services, managed services, security reporting, security threats, security
Posted in: Managed IT Services, Security
December 7th, 2016 by admin
If your company’s antivirus software is letting you down, you should think twice before installing a second one on a computer: It may actually make things worse.
Multiple antivirus programs working in conjunction on the same device is not a case of...
Read Full Story »
Tags: anti-virus, backup, Backup Solutions, cyber security, disaster recovery, IT Consulting, IT Security, IT Support , IT, security threats, security
Posted in: Security
November 23rd, 2016 by admin
In September 2016, half a billion Yahoo account users received the bad news that their names, email addresses, phone numbers, and security questions were potentially stolen in a 2014 hack.
According to CNET, the Yahoo hack is the largest data breach...
Read Full Story »
Tags: cyber security, hacking, IT Consulting, IT Security, IT, password, security threats, security
Posted in: Security
November 1st, 2016 by admin
As you probably know already, the United States experienced its largest Internet blackout in history on October 21, 2016, when Dyn—a service that handles website domain name routing—got hit with a massive distributed denial of service (DDoS) attack...
Read Full Story »
Tags: IT Consulting, IT Security, IT Support , IT, network security, network, security threats, security
Posted in: Backup, Security
August 30th, 2016 by admin
Those old servers your business no longer uses—and keeps running anyway—are more than just a security risk: They’re hurting your firm’s bottom line.
The term comatose server describes a functional server, connected to a network, that sits idle virtually...
Read Full Story »
Tags: advice, security threats, security, servers
Posted in: Solutions, Knowledge
August 9th, 2016 by admin
There was a time when printers—in your office or home—were considered relatively "simple" office equipment: plug it in, connect it to the local network, and keep the ink fresh, and there wasn't much else to worry about.
But times have changed.
Today's...
Read Full Story »
Tags: network security, security threats, security
Posted in: Managed IT Services, Knowledge
July 12th, 2016 by admin
If you've looked over our previous posts since we've started our blog, you know how serious we are about protecting your company from everyday cyber-threats—mainly phishing, ransomware, and various other malware. Today we'd like to discuss a different...
Read Full Story »
Tags: cyber security, malware, network security, network, ransomware, security threats, security
Posted in: Managed IT Services, Solutions, Knowledge
July 7th, 2016 by admin
It's a fair bet that one of your employees has already shown off a trendy new wearable gadget around the office. What began with Bluetooth earpieces would branch off into smartwatches, smart glasses, wrist-worn fitness trackers, and even smart clothing...
Read Full Story »
Tags: devices, password, security threats, security
Posted in: Managed IT Services, Security, Knowledge
June 29th, 2016 by admin
Readers of our blog over the past few years know we were among the first in the Bay Area to warn our customers about the growing threats of ransomware—from the emergence of CryptoLocker and CryptoWall to our federal government's startling admission...
Read Full Story »
Tags: anti-virus, consulting, cyber security, data security, ransomware, security threats, security
Posted in: Support, Security, Knowledge
June 14th, 2016 by admin
A WISP is one of the most important documents for any company doing business over the Internet—which, in this day and age, is pretty much everybody. Who's responsible for drafting and maintaining your company's WISP? Or are you even sure what a WISP...
Read Full Story »
Tags: data protection, data security, security threats, security
Posted in: Security, Knowledge
June 1st, 2016 by admin
Being the cyber-security geeks we are, we took great interest in combing through this year's California Data Breach Report, released by the Attorney General's office this past February. The report tabulates data collected from breach incidents which...
Read Full Story »
Tags: cyber security, data protection, data security, malware, ransomware, security threats, security
Posted in: Data, Security
May 11th, 2016 by admin
Smartphone users can be broken down into two camps: those who can't live without lining up to buy the latest and greatest model the day it hits the stores, and those who hold on to their tried-and-true phone until it suddenly dies one morning.
There's...
Read Full Story »
Tags: advice, mobile, security threats, security, smartphones
Posted in: Security, Knowledge
May 3rd, 2016 by admin
Today we'd like to pass along a critical security advisory to all our customers:
If any of your company's Windows systems still retain Apple's QuickTime for Windows software, uninstall it immediately—as soon as you finish reading this post (if not...
Read Full Story »
Tags: advice, end of life, hacking, security threats, security
Posted in: Support, Security, Knowledge
April 26th, 2016 by admin
Earlier today the cashier at the local drive-thru miskeyed the amount of cash I gave him into his register. Somewhat sheepishly, he asked if I had a smartphone so I could verify the correct amount of change. Fortunately, I never leave home without it....
Read Full Story »
Tags: IT Consulting, IT Support , IT, mobility, security threats, security, smartphones
Posted in: Managed IT Services, Support, Knowledge
April 12th, 2016 by admin
A couple months back, we touched on the story of our normally tech-savvy friend who got tricked into allowing his desktop PC to be infected with obvious malware. At first, he had the sickening feeling that comes with a virus-infected computer—but thanks...
Read Full Story »
Tags: anti-virus, cyber security, malware, security threats, security
Posted in: Security
April 7th, 2016 by admin
We're only a few months into 2016, but we've already seen two high-profile ransomware attacks—where cyber-crooks heavily encrypt a victim's computer files before demanding payment for a decryption key only they can provide. Two notable incidents grabbed...
Read Full Story »
Tags: backup, Backup Solution, cyber security, ransomware, security threats, security
Posted in: Backup, Security, Knowledge
March 30th, 2016 by admin
If you think there's a new cyber-threat to worry about every week, you're probably right. The latest vulnerability to send shockwaves through the enterprise security community has been given a rather ominous acronym: DROWN, short for Decrypting RSA...
Read Full Story »
Tags: anti-virus, cyber security, hacking, security threats, security
Posted in: Security, Knowledge
March 23rd, 2016 by admin
Since Apple famously introduced the Macintosh over three decades ago, Mac users have been confident that their computers are virtually immune to ransomware and other malware threats which plague their Windows counterparts. But those days are over.
...
Read Full Story »
Tags: cyber security, hacking, malware, ransomware, security threats, security
Posted in: Security, Knowledge
March 15th, 2016 by admin
Hackers can take advantage of a newer technology prevalent throughout your business to break into your network and compromise security: Internet of Things devices. Your business may have never considered that the handy new Smart Thermostats throughout...
Read Full Story »
Tags: hacking, IT Consulting, IT Security, IT, security threats, security, smart devices
Posted in: Security
March 8th, 2016 by admin
February's big story in the tech world was the conflict between Apple and the FBI over the creation of a "backdoor" to retrieve encrypted data on iPhones. The government is looking for any clue as to what—or, more specifically, who—motivated Syed Farook,...
Read Full Story »
Tags: mobile, security
Posted in: Security
January 5th, 2016 by admin
What is the current state of your company's IT security training program—if you have one? Many companies settle for an annual group training session to broadly review the major types of cyber-threats—viruses, malware, and phishing.
The problem with...
Read Full Story »
Tags: cyber security, managed IT services, managed services, security threats, security, training
Posted in: Security
July 15th, 2015 by admin
While video surveillance does help to protect your business from crime, that is not all it does. It also...
Protects your staff in case of customer disputes
Enforces safe work conditions
allows you to see whether procedures and protocols are being...
Read Full Story »
Tags: ATS Communications, security, services, surveillance
Posted in: Security
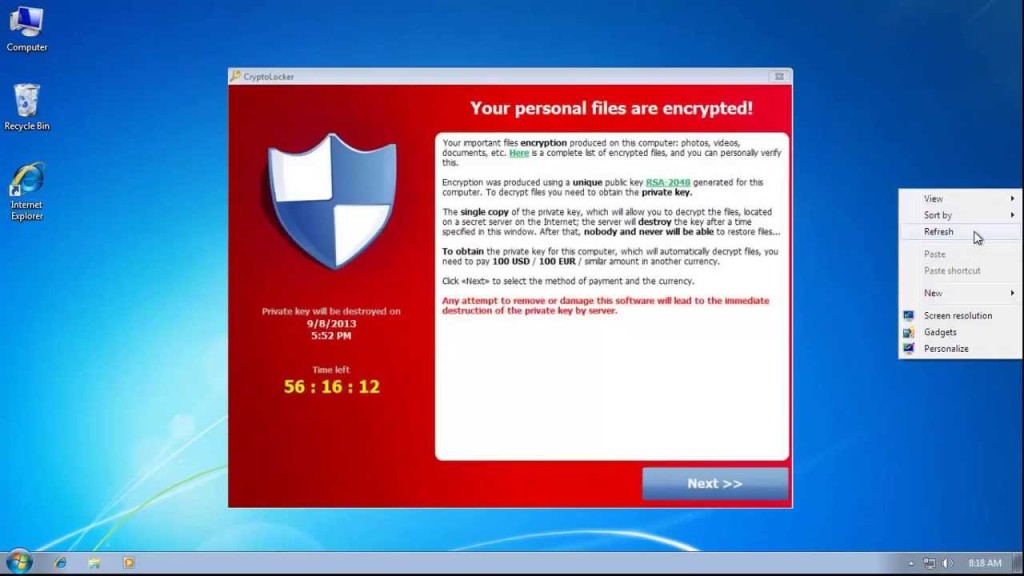
November 15th, 2013 by admin
CryptoLocker
CryptoLocker is a new, and particularly malicious, breed of ransomware discovered only a couple months ago. CryptoLocker is a Trojan horse malware that encrypts and restricts access to the infected computer while demanding payment for...
Read Full Story »
Tags: cyber security, ransomware, security threats, security
Posted in: Data, Security
September 30th, 2013 by admin
Partnering with a Managed Service Provider (MSP) is one of the most important decisions you can make to ensure the longevity and productivity of your SMB. Why? An experienced MSP is a true business partner, reduces and streamlines IT costs, and takes...
Read Full Story »
Tags: Backup Solution, desktop management, IT budgeting, IT Consulting, IT purchasing, IT Security, IT Support , IT, managed IT services, managed services, security reporting, security
Posted in: Managed IT Services